The Best Defense Are Your Employees
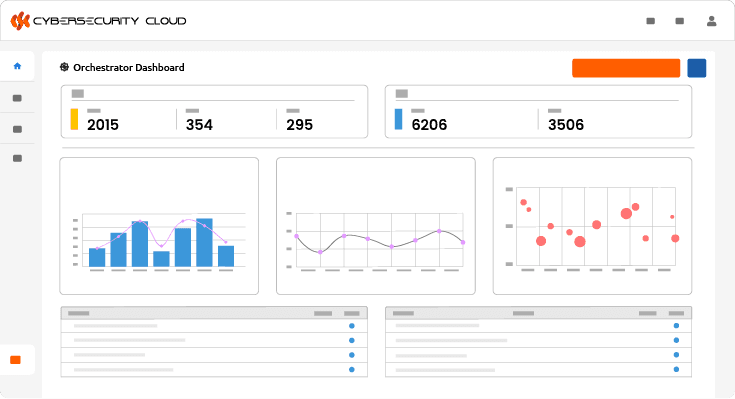
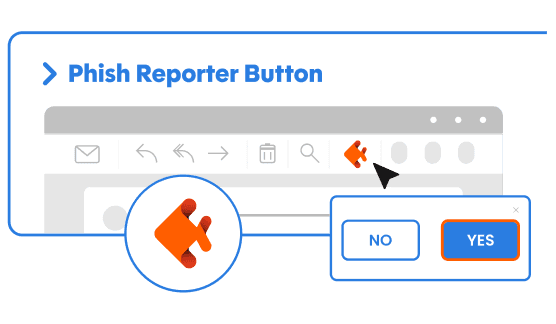
Transform Phishing Reports into Automated, Intelligence-Driven Response Workflows. Orchestrator enables security operations teams to automatically ingest, analyze, prioritize, and respond to user-reported phishing threats — cutting triage times from hours to minutes while reducing noise and manual effort.